2016 October Cisco Official New Released 300-115 Dumps in Lead2pass.com!
100% Free Download! 100% Pass Guaranteed!
300-115 easy pass guide: Preparing for Cisco 300-115 exam is really a tough task to accomplish. However, Lead2pass delivers the most comprehensive braindumps, covering each and every aspect of 300-115 exam curriculum.
Following questions and answers are all new published by Cisco Official Exam Center: http://www.lead2pass.com/300-115.html
QUESTION 141
Refer to the exhibit. What is the result of the configuration?
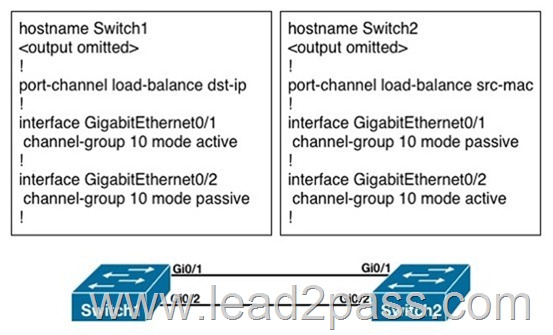
A. The EtherChannels would not form because the load-balancing method must match on the devices.
B. The EtherChannels would form and function properly even though the load-balancing and EtherChannel modes do not match.
C. The EtherChannels would form, but network loops would occur because the load- balancing methods do not match.
D. The EtherChannels would form and both devices would use the dst-ip load-balancing method because Switch1 is configured with EtherChannel mode active.
Answer: B
QUESTION 142
A network engineer tries to configure storm control on an EtherChannel bundle. What is the result of the configuration?
A. The storm control settings will appear on the EtherChannel, but not on the associated physical ports.
B. The configuration will be rejected because storm control is not supported for EtherChannel.
C. The storm control configuration will be accepted, but will only be present on the physical interfaces.
D. The settings will be applied to the EtherChannel bundle and all associated physical interfaces.
Answer: D
QUESTION 143
A Cisco Catalyst switch that is prone to reboots continues to rebuild the DHCP snooping database. What is the solution to avoid the snooping database from being rebuilt after every device reboot?
A. A DHCP snooping database agent should be configured.
B. Enable DHCP snooping for all VLANs that are associated with the switch.
C. Disable Option 82 for DHCP data insertion.
D. Use IP Source Guard to protect the DHCP binding table entries from being lost upon rebooting.
E. Apply ip dhcp snooping trust on all interfaces with dynamic addresses.
Answer: A
QUESTION 144
Which portion of AAA looks at what a user has access to?
A. authorization
B. authentication
C. accounting
D. auditing
Answer: A
QUESTION 145
Which command creates a login authentication method named “login” that will primarily use RADIUS and fail over to the local user database?
A. (config)# aaa authentication login default radius local
B. (config)# aaa authentication login login radius local
C. (config)# aaa authentication login default local radius
D. (config)# aaa authentication login radius local
Answer: B
QUESTION 146
What is the function of NSF?
A. forward traffic simultaneously using both supervisors
B. forward traffic based on Cisco Express Forwarding
C. provide automatic failover to back up supervisor in VSS mode
D. provide nonstop forwarding in the event of failure of one of the member supervisors
Answer: D
QUESTION 147
Which configuration command ties the router hot standby priority to the availability of its interfaces?
A. standby group
B. standby priority
C. backup interface
D. standby track
Answer: D
QUESTION 148
What is the default HSRP priority?
A. 50
B. 100
C. 120
D. 1024
Answer: B
QUESTION 149
A server with a statically assigned IP address is attached to a switch that is provisioned for DHCP snooping. For more protection against malicious attacks, the network team is considering enabling dynamic ARP inspection alongside DHCP snooping. Which solution ensures that the server maintains network reachability in the future?
A. Disable DHCP snooping information option.
B. Configure a static DHCP snooping binding entry on the switch.
C. Trust the interface that is connected to the server with the ip dhcp snooping trust command.
D. Verify the source MAC address of all untrusted interfaces with ip dhcp snooping verify mac-address command.
Answer: B
QUESTION 150
DHCP snooping and IP Source Guard have been configured on a switch that connects to several client workstations. The IP address of one of the workstations does not match any entries found in the DHCP binding database. Which statement describes the outcome of this scenario?
A. Packets from the workstation will be rate limited according to the default values set on the switch.
B. The interface that is connected to the workstation in question will be put into the errdisabled state.
C. Traffic will pass accordingly after the new IP address is populated into the binding database.
D. The packets originating from the workstation are assumed to be spoofed and will be discarded.
Answer: D
QUESTION 151
Which technique allows specific VLANs to be strictly permitted by the administrator?
A. VTP pruning
B. transparent bridging
C. trunk-allowed VLANs
D. VLAN access-list
E. L2P tunneling
Answer: C
QUESTION 152
For security reasons, the IT manager has prohibited users from dynamically establishing trunks with their associated upstream switch. Which two actions can prevent interface trunking? (Choose two.)
A. Configure trunk and access interfaces manually.
B. Disable DTP on a per interface basis.
C. Apply BPDU guard and BPDU filter.
D. Enable switchport block on access ports.
Answer: AB
QUESTION 153
Which two protocols can be automatically negotiated between switches for trunking? (Choose two.)
A. PPP
B. DTP
C. ISL
D. HDLC
E. DLCI
F. DOT1Q
Answer: CF
QUESTION 154
A network is running VTPv2. After verifying all VTP settings, the network engineer notices that the new switch is not receiving the list of VLANs from the server. Which action resolves this problem?
A. Reload the new switch.
B. Restart the VTP process on the new switch.
C. Reload the VTP server.
D. Verify connected trunk ports.
Answer: D
QUESTION 155
After configuring new data VLANs 1020 through 1030 on the VTP server, a network engineer notices that none of the VTP clients are receiving the updates. What is the problem?
A. The VTP server must be reloaded.
B. The VTP version number must be set to version 3.
C. After each update to the VTP server, it takes up to 4 hours propagate.
D. VTP must be stopped and restarted on the server.
E. Another switch in the domain has a higher revision number than the server.
Answer: B
QUESTION 156
A network engineer is extending a LAN segment between two geographically separated data centers. Which enhancement to a spanning-tree design prevents unnecessary traffic from crossing the extended LAN segment?
A. Modify the spanning-tree priorities to dictate the traffic flow.
B. Create a Layer 3 transit VLAN to segment the traffic between the sites.
C. Use VTP pruning on the trunk interfaces.
D. Configure manual trunk pruning between the two locations.
Answer: C
Explanation:
Pruning unnecessary VLANs from the trunk can be performed with one of two methods:
• Manual pruning of the unnecessary VLAN on the trunk – This is the best method, and it avoids the use of the spanning tree. Instead, the method runs the pruned VLAN on trunks.
• VTP pruning – Avoid this method if the goal is to reduce the number of STP instances.
VTP-pruned VLANs on a trunk are still part of the spanning tree. Therefore, VTP-pruned VLANs do not reduce the number of spanning tree port instances.
Since the question asked for the choice that is an enhancement to the STP design, VTP pruning is the best choice.
http://www.cisco.com/en/US/tech/tk389/tk689/technologies_tech_note09186a0080890613.shtml
QUESTION 157
The network manager has requested that several new VLANs (VLAN 10, 20, and 30) are allowed to traverse the switch trunk interface. After the command switchport trunk allowed vlan 10,20,30 is issued, all other existing VLANs no longer pass traffic over the trunk. What is the root cause of the problem?
A. The command effectively removed all other working VLANs and replaced them with the new VLANs.
B. VTP pruning removed all unused VLANs.
C. ISL was unable to encapsulate more than the already permitted VLANs across the trunk.
D. Allowing additional VLANs across the trunk introduced a loop in the network.
Answer: A
QUESTION 158
When you design a switched network using VTPv2, how many VLANs can be used to carry user traffic?
A. 1000
B. 1001
C. 1024
D. 2048
E. 4095
F. 4096
Answer: B
QUESTION 159
What does the command vlan dot1q tag native accomplish when configured under global configuration?
A. All frames within the native VLAN are tagged, except when the native VLAN is set to 1.
B. It allows control traffic to pass using the non-default VLAN.
C. It removes the 4-byte dot1q tag from every frame that traverses the trunk interface(s).
D. Control traffic is tagged.
Answer: D
QUESTION 160
Which private VLAN access port belongs to the primary VLAN and can communicate with all interfaces, including the community and isolated host ports?
A. promiscuous port
B. isolated port
C. community port
D. trunk port
Answer: A
Lead2pass provides guarantee of Cisco 300-115 exam because Lead2pass is an authenticated IT certifications site. The 300-115 dump is updated with regular basis and the answers are rechecked of every exam. Good luck in your exam.
300-115 new questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDS21vUTdBQVgxWFk
2016 Cisco 300-115 exam dumps (All 230 Q&As) from Lead2pass:
http://www.lead2pass.com/300-115.html [100% Exam Pass Guaranteed]